From Mandiant, a US cyber-security consultancy, comes some damning accusations on China’s corporate espionage:
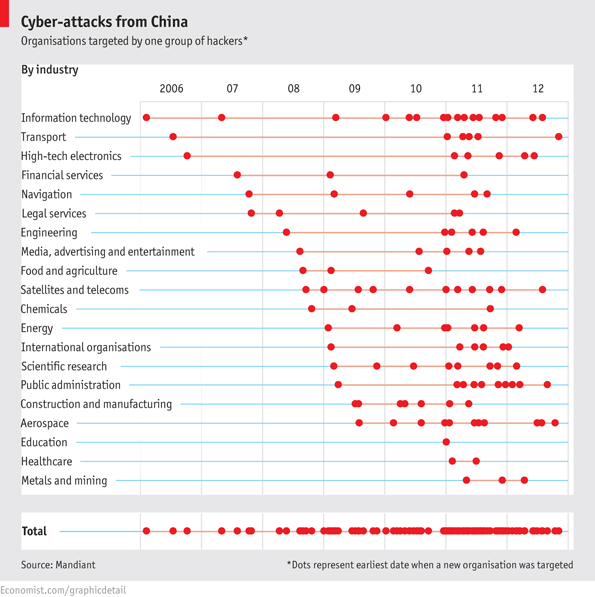
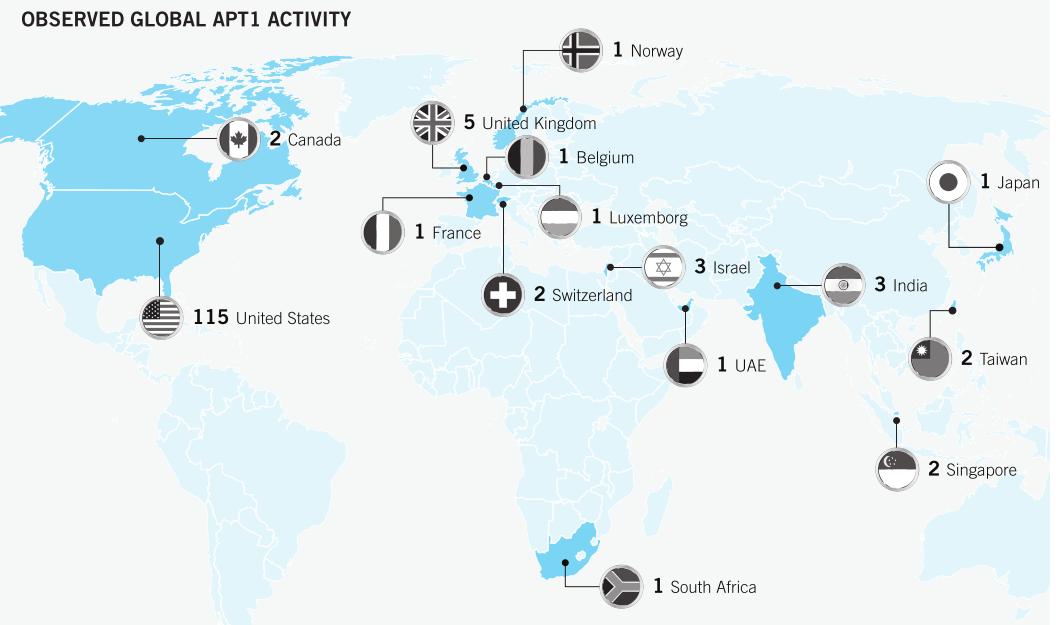
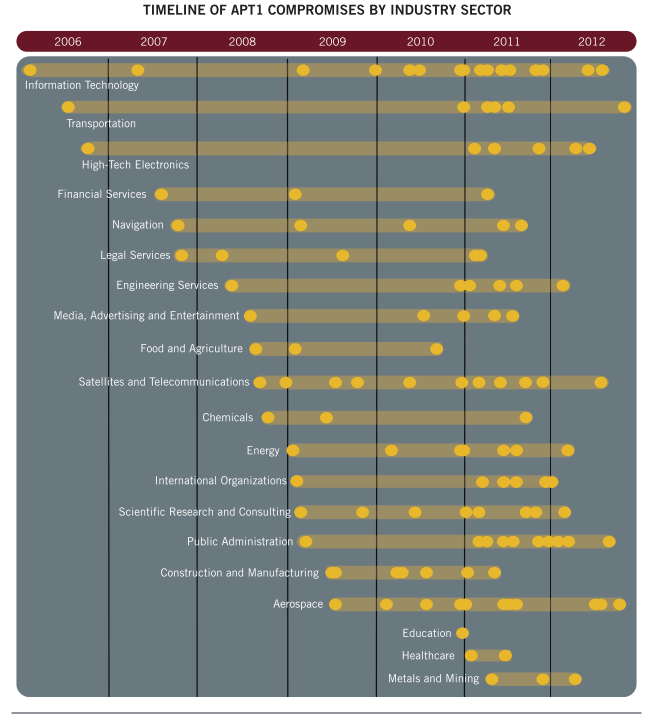
The [Chinese Government] has demonstrated the capability and intent to steal from dozens of organizations across a wide range of industries virtually simultaneously. Figure below provides a view of the earliest known date of [government espionage] activity against all of the 141 victims we identified, organized by the 20 major industries they represent. The results suggest that APT1’s mission is extremely broad; the group does not target industries systematically but more likely steals from an enormous range of industries on a continuous basis. Since the organizations included in the figure represent only the fraction of APT1 victims that we confirmed directly, the range of industries that APT1 targets may be even broader than our findings suggest.
More charts after the jump
Hack-attack
Source: Economist.com


What's been said:
Discussions found on the web: